Primera parte:
Ping: Utiliza la herramienta ping desde la terminal de tu ordenador para comprobar si están disponibles los siguientes hosts:
http://www.google.es (O cualquier otra dirección conocida).
http://www.euskalert.net
O bien puedes optar por un servidor web de internet de tu elección.
Solución:
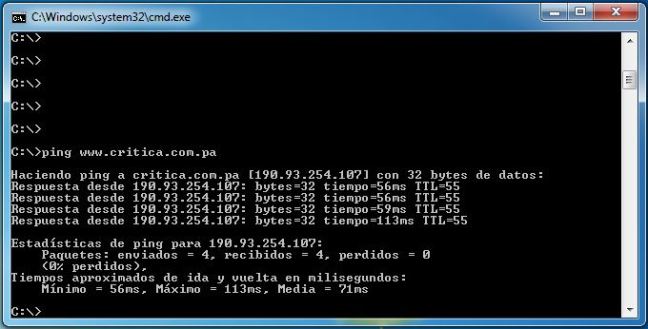
- Ping critica.com.pa
Segunda parte:
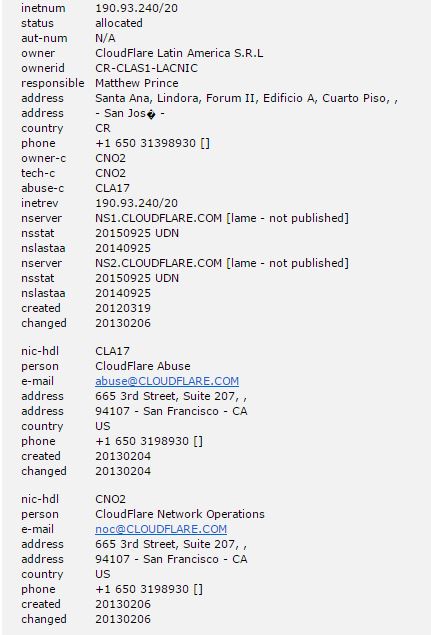
Whois: Comprueba si esta herramienta está disponible para tu Sistema Operativo. Si es así descárgala y si no usa su versión online (http://ping.eu/ns-whois/). A continuación busca información sobre el dominio que estás investigando. Encuentra la persona que figura como contacto técnico y como contacto administrativo. Esta información puede servir a un hacker para contactar directamente con las personas adecuadas dentro de la empresa (nota: Kevin Mitnick era un experto en colarse en las empresas vestido con un uniforme de asistencia técnica y preguntando por las personas adecuadas).
Solución
Tercera Parte
Nmap: Descarga la herramienta Nmap y analiza alguna de las anteriores direcciones. A continuación explica qué puertos están abiertos y cuál puede ser la razón. Nmap también intenta identificar los sistemas operativos y las aplicaciones que están corriendo en el servidor que estás investigando. Identifica alguna aplicación en el servidor y consulta en la página de la Base de Datos de Vulnerabilidades Nacional de Estados Unidos (NVD) a cuántas vulnerabilidades está expuesto.
Solución
| Starting Nmap 6.49BETA5 ( https://nmap.org ) at 2015-09-25 14:53 Hora est. Pacífico, Sudamérica NSE: Loaded 122 scripts for scanning. NSE: Script Pre-scanning. Initiating NSE at 14:53 Completed NSE at 14:53, 0.01s elapsed Initiating NSE at 14:53 Completed NSE at 14:53, 0.00s elapsed Initiating Ping Scan at 14:53 Scanning critica.com.pa (190.93.255.107) [4 ports] Completed Ping Scan at 14:53, 1.04s elapsed (1 total hosts) Initiating Parallel DNS resolution of 1 host. at 14:53 Completed Parallel DNS resolution of 1 host. at 14:53, 0.13s elapsed Initiating SYN Stealth Scan at 14:53 Scanning critica.com.pa (190.93.255.107) [1000 ports] Discovered open port 8080/tcp on 190.93.255.107 Discovered open port 443/tcp on 190.93.255.107 Discovered open port 80/tcp on 190.93.255.107 Discovered open port 8443/tcp on 190.93.255.107 Completed SYN Stealth Scan at 14:53, 28.09s elapsed (1000 total ports) Initiating Service scan at 14:53 Scanning 4 services on critica.com.pa (190.93.255.107) Completed Service scan at 14:54, 13.04s elapsed (4 services on 1 host) Initiating OS detection (try #1) against critica.com.pa (190.93.255.107) Initiating Traceroute at 14:54 Completed Traceroute at 14:54, 3.09s elapsed Initiating Parallel DNS resolution of 10 hosts. at 14:54 Completed Parallel DNS resolution of 10 hosts. at 14:54, 5.57s elapsed NSE: Script scanning 190.93.255.107. Initiating NSE at 14:54 Completed NSE at 14:54, 9.69s elapsed Initiating NSE at 14:54 Completed NSE at 14:54, 0.00s elapsed Nmap scan report for critica.com.pa (190.93.255.107) Host is up (0.092s latency). Other addresses for critica.com.pa (not scanned): 190.93.254.107 2400:cb00:2048:1::be5d:ff6b 2400:cb00:2048:1::be5d:fe6b Not shown: 996 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Cloudflare nginx |_http-favicon: Unknown favicon MD5: BBEBD33C3EB3649E248B301B5750236C |_http-generator: Drupal 7 (http://drupal.org) |_http-methods: No Allow or Public header in OPTIONS response (status code 301) | http-robots.txt: 44 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |_/LICENSE.txt /MAINTAINERS.txt |_http-server-header: cloudflare-nginx | http-title: Critica | Noticias y Novedades de Panam\xC3\xA1 y el Mundo |_Requested resource was http://www.critica.com.pa/ 443/tcp open ssl/http Cloudflare nginx | http-cisco-anyconnect: |_ ERROR: Not a Cisco ASA or unsupported version |_http-methods: No Allow or Public header in OPTIONS response (status code 400) |_http-server-header: cloudflare-nginx |_http-title: Did not follow redirect to http://www.critica.com.pa/ | ssl-cert: Subject: commonName=ssl84427.cloudflare.com/organizationName=CloudFlare, Inc./stateOrProvinceName=California/countryName=US | Issuer: commonName=GlobalSign Organization Validation CA – G2/organizationName=GlobalSign nv-sa/countryName=BE | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2015-08-28T16:01:27 | Not valid after: 2015-11-28T22:59:18 | MD5: a89a b314 a1fb 6a86 8d71 4493 f4a9 703c |_SHA-1: 7f84 ed05 f7a8 3358 76ac a2c0 755c a90a 01a6 df12 |_ssl-date: TLS randomness does not represent time | tls-nextprotoneg: | spdy/3.1 |_ http/1.1 8080/tcp open http Cloudflare nginx |_http-methods: No Allow or Public header in OPTIONS response (status code 301) |_http-server-header: cloudflare-nginx |_http-title: Did not follow redirect to http://www.critica.com.pa/ 8443/tcp open ssl/http Cloudflare nginx | http-cisco-anyconnect: |_ ERROR: Not a Cisco ASA or unsupported version |_http-methods: No Allow or Public header in OPTIONS response (status code 521) |_http-server-header: cloudflare-nginx |_http-title: critica.com.pa | 521: Web server is down | ssl-cert: Subject: commonName=ssl84427.cloudflare.com/organizationName=CloudFlare, Inc./stateOrProvinceName=California/countryName=US | Issuer: commonName=GlobalSign Organization Validation CA – G2/organizationName=GlobalSign nv-sa/countryName=BE | Public Key type: rsa | Public Key bits: 2048 | Signature Algorithm: sha1WithRSAEncryption | Not valid before: 2015-08-28T16:01:27 | Not valid after: 2015-11-28T22:59:18 | MD5: a89a b314 a1fb 6a86 8d71 4493 f4a9 703c |_SHA-1: 7f84 ed05 f7a8 3358 76ac a2c0 755c a90a 01a6 df12 |_ssl-date: TLS randomness does not represent time | tls-nextprotoneg: | spdy/3.1 |_ http/1.1 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running: Linux 3.X OS CPE: cpe:/o:linux:linux_kernel:3 OS details: Linux 3.12 Network Distance: 11 hops TCP Sequence Prediction: Difficulty=261 (Good luck!) IP ID Sequence Generation: All zeros TRACEROUTE (using port 8080/tcp) HOP RTT ADDRESS 1 0.00 ms 192.168.1.1 2 … 3 20.00 ms 10.48.41.57 4 20.00 ms 10.48.42.9 5 20.00 ms 10.48.40.94 6 20.00 ms 10.10.11.2 7 20.00 ms 10.48.40.98 8 20.00 ms 10.48.41.237 9 70.00 ms 63.245.3.97 10 100.00 ms 198.32.125.60 11 60.00 ms 190.93.255.107 NSE: Script Post-scanning. Initiating NSE at 14:54 Completed NSE at 14:54, 0.00s elapsed Initiating NSE at 14:54 Completed NSE at 14:54, 0.00s elapsed Read data files from: C:\Program Files\Nmap OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 73.66 seconds Raw packets sent: 2071 (92.906KB) | Rcvd: 86 (4.226KB) |
Puertos abiertos:
- Discovered open port 8080/tcp on 190.93.255.107
- HTTP HTTP-ALT ver puerto 80. Tomcat lo usa como puerto por defecto.
- Discovered open port 443/tcp on 190.93.255.107
- HTTPS/SSL usado para la transferencia segura de páginas web
- Discovered open port 80/tcp on 190.93.255.107
- HTTP HyperText Transfer Protocol (Protocolo de Transferencia de HiperTexto) (WWW)
- Discovered open port 8443/tcp on 190.93.255.107
- Garantiza la entrega de paquetes de datos en la misma orden, en que fueron mandados.
Sistema operativo y Gestor de contenidos
- OS details: Linux 3.12
- Gestor de Contenidos: Dupral
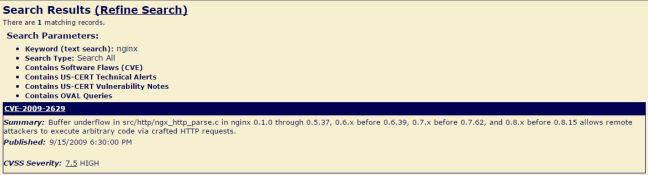
Tiene su sitio web asegurado con la plataforma de «Cloudflare nginx» por lo que la búsqueda de «nginx» en la NVD arrojó los siguientes resultados: